HYAS Protect R24.11
Release # | UI: R24.11, Agent: N/A |
|---|---|
Date |
What's New in HYAS Protect!
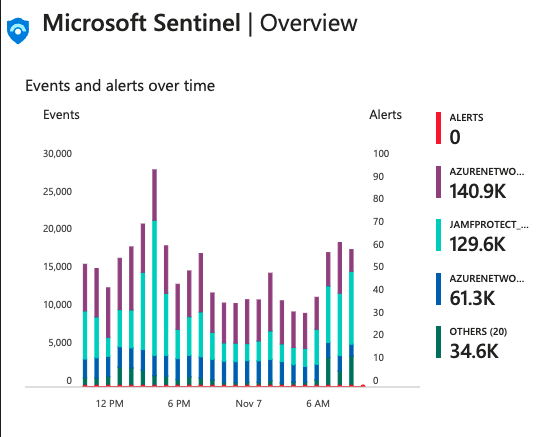
Microsoft Sentinel Integration NEW
HYAS Protect now integrates with Microsoft Sentinel, bringing enriched DNS-layer data into the Sentinel SIEM environment. This integration allows security teams to access and correlate HYAS Protect logs within their centralized Sentinel workspace, enhancing visibility, threat detection, and automated incident response capabilities. Security teams can perform advanced threat hunting using custom KQL searches, automate incident responses through Sentinel’s SOAR capabilities, and create tailored dashboards and reports to visualize critical DNS security metrics in real-time.
Benefits:
Enhanced Threat Detection and Correlation: Integrating HYAS Protect logs with Sentinel improves visibility into DNS traffic, enabling better detection and correlation of potential threats within a centralized workspace.
Advanced Threat Hunting Capabilities: Use custom KQL searches in Sentinel to perform deep analysis of DNS data, identifying stealthy threats and patterns not easily detected by standalone solutions.
Automated Incident Response: Leverage Sentinel’s SOAR capabilities to automate responses based on HYAS Protect logs, speeding up containment actions like device quarantine and alerting key personnel.
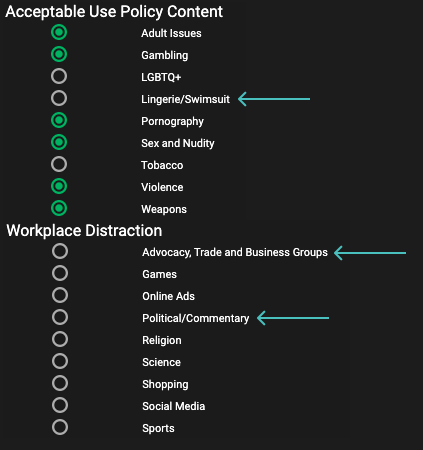
Enhanced Content Filtering Precision IMPROVEMENT
The Enhanced Content Filtering Precision feature provides clients with greater control over content filtering categories, enabling the definition and customization of policies with increased granularity. This allows organizations to tailor which content is accessible or blocked, aligning security settings with specific needs to improve overall security, compliance, and user browsing safety.
Benefits:
Granular Control Over Content: Precisely define and customize content filtering policies to better align with organizational requirements.
Improved Security and Compliance: Tailor accessible and blocked content to enhance security posture and ensure compliance with internal policies or regulations.
Optimized User Experience: Create a safer and more focused browsing environment tailored to user needs.
Malicious Cyber Activity Renamed to Threats IMPROVEMENT
“Malicious Cyber Activity” is now known as “Threats” in HYAS Protect. This includes policies, log view and aggregated log view.

Benefits:
Increased Clarity & Consistency: “Threats” is a more widely recognized term in the industry, making it easier for clients to quickly identify and understand the threats within HYAS Protect and the value it provides by detecting/identifying them.
