Splunk Enterprise
Overview
The HYAS Protect integration with Splunk delivers a user-friendly experience for accessing threat intelligence within the Splunk environment. Once configured, users can seamlessly navigate the built-in Protect dashboard, where selecting the indicator type and inputting the value yields the HYAS Protect verdict. Additionally, advanced commands for domain, FQDN, nameserver, and IP address verdicts are available, facilitating effortless integration into custom searches and dashboards. For Splunk's Enterprise Security users, an adaptive response action within the Incident Review view enables the selection of notable events and the execution of Protect queries. This integration empowers users to efficiently harness HYAS Protect's threat intelligence capabilities directly within the Splunk environment, enhancing their ability to investigate and respond to security incidents effectively.
Prerequisites
Windows or Linux operating system.
Installation
Download
Download HYAS Protect for Splunk from https://splunkbase.splunk.com/app/6474/
Installation steps
To install and configure this app on your supported platform, follow these steps:
Download app from Splunkbase
Place [hyas-protect-for-splunk_101.tgz] somewhere on your Search Head
Install using splunk command:
CODEsplunk install app /path/to/hyas-protect-for-splunk_101.tgzSet API key. This can be done in Splunkweb by clicking "Setup" in the app's navigation bar.
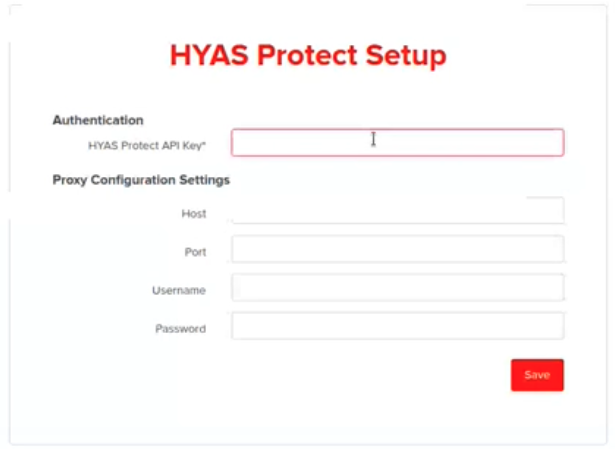
Configuration
The only configuration needed for this app is setting an API key. This can be done in Splunkweb by clicking "Set up" on the "Manage apps" page, or through command line by editing password.conf.
User Guide
Usage
Once configured, the easiest way to use this app is through the built-in Protect dashboard. Select indicator type and type indicator value and press enter.
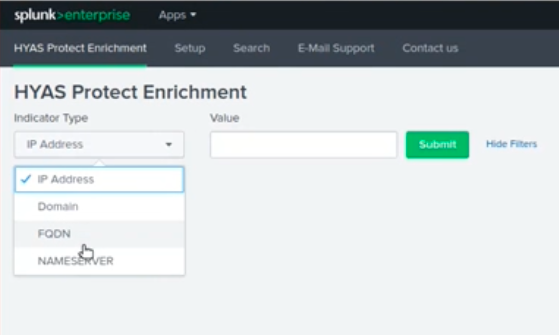
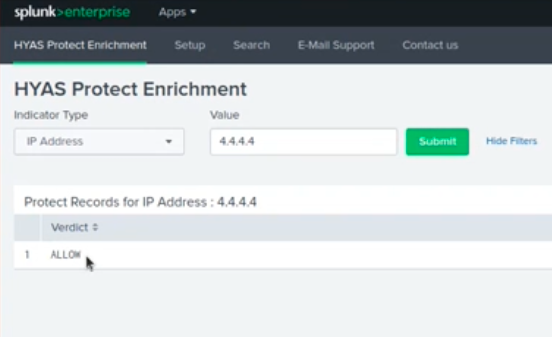
HYAS Protect for Splunk also comes with multiple commands and a lookup so that you can incorporate Protect queries into your own searches and dashboards. Below is usage documentation for all four (4) verdict types that can be solicited.
Verdicts
Domain Verdict
Runs this command to get the HYAS Protect verdict for domain.
| hyasprotectverdictfordomain value=fishfarm.duckdns.org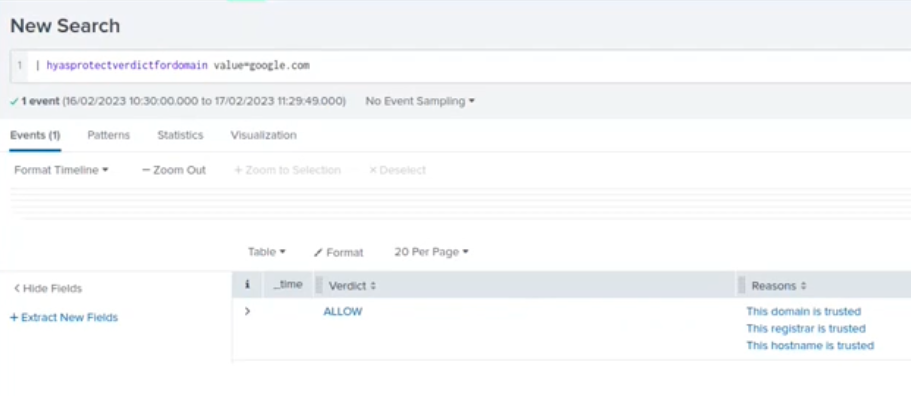
FQDN Verdict
Runs this command to get the HYAS Protect verdict for FQDN.
| hyasprotectverdictforfqdn value=www.fishfarm.duckdns.orgNameserver Verdict
Runs this command to get the HYAS Protect verdict for nameserver.
| hyasprotectverdictfornameserver value=ns2.duckdns.orgIP Address Verdict
Runs this command to get the HYAS Protect verdict for IP.
| hyasprotectverdictforip value=23.129.64.139Adaptive response action
If you use Splunk's Enterprise Security product, this app includes an adaptive response action which can be used from the Incident Review view. Select any notable event you wish to run a Protect query against, select "Run Adaptive Response Actions" and then "Protect Lookup". Select the indicator type from dropdown (ip address, domain, fqdn, nameserver), type of the value of indicator (eg.1.1.1.1) and any other inputs needed. Click "Run", and then refresh the adaptive responses panel of that notable events. Clicking "Protect Lookup" in that panel will send you to a search containing the output of your lookup.
